My Take on OSCP Certification

So it's been a few days now since I received my OSCP results and since then my inbox is a buzzing with all the query regarding OSCP. So, I thought why not write a blog about it like everybody else. This is not a OSCP Review
How it started...
It was late August and I decided to start preparing for PWK. I had many questions about the course
- Where to start.
- What to focus more on.
- BIGGEST ONE - AM I READY FOR THE COURSE, as I had only 1.5 years of experience in this field and people who have been on the profession long can't clear the certification in first go. I started reading multiple blogs and reviews about OSCP.
How others prepared where they failed and what mistakes they did. I read many blogs and made notes and a preparation methodology:
- Buffer Overflow
- Web Exploits
- Windows Attacks
- Linux Attacks
- Crack few Vulnhub's
- Crack few Hack the Box Machines
For Buffer Overflow:
- Pentesters Academy Exploiting Simple Buffer Overflows on Win32.
- Found a list of exploitable applications on "whitelist1.com"
Scripts mostly used by me:
- LinEnum.sh
- Privchecker.py
- Windows Exploit Suggestor
- Just Another Windows (Enum) Script
After months of practice finally opted for PWK in November and the labs had to start from December.
JOIN TONS OF CHAT GROUPS RELATED TO OSCP
The Courseware!!!
The day came for my labs to start. I received the mail at 5:42 am. I quickly downloaded the course material. A lot! About 380 pages of pure written PDF and endless hours of video material. Great stuff – nothing more to say, but no pain until here. Once my labs started I studied 5-6 hours in weekday and 8-10 hours on weekends. I completed my videos and PDF pretty fast as I copied the material on my phone too. I used to watch and read whenever I had time during the day.
The Labs!!!
Now comes the scary part. I had heard from my peers that the starting machines are pretty easy. Multiple machines can be knocked down in a single day. I couldn't solve the first machine on the first day. I got the machine on the second day. It was de-moralizing. Later I went on to crack 85% of the lab machines in span of 2 months.  The labs changed my perspective to view the machine as a whole, the approach to attack the machine. I won't talk about the machine in the lab, there are tons of blogs where you can read about them.
The labs changed my perspective to view the machine as a whole, the approach to attack the machine. I won't talk about the machine in the lab, there are tons of blogs where you can read about them.
The Exam...
Reading from all the blogs and reviews I came up with a plan to give the exam the midway of my labs. This would allow me to practice more if I failed my first attempt. Also, this would save me from spending money on the extra lab days. I will have to pay a minimal fee to re-take the exam which is affordable. My exam started at 11:30 am and by night at 8:30 pm I had enough points to pass the exam. I gave a try on the last machine but due to day-long mental exhaustion, I was tired. I tried a bit more till 10:00 pm and paused my VPN connection. After a little break, I started on reporting I had found that my screenshots were not proper. A piece of advice.
Once you have enough passing marks start on your report. Double Check, Triple Check the screenshots.
And few days later....
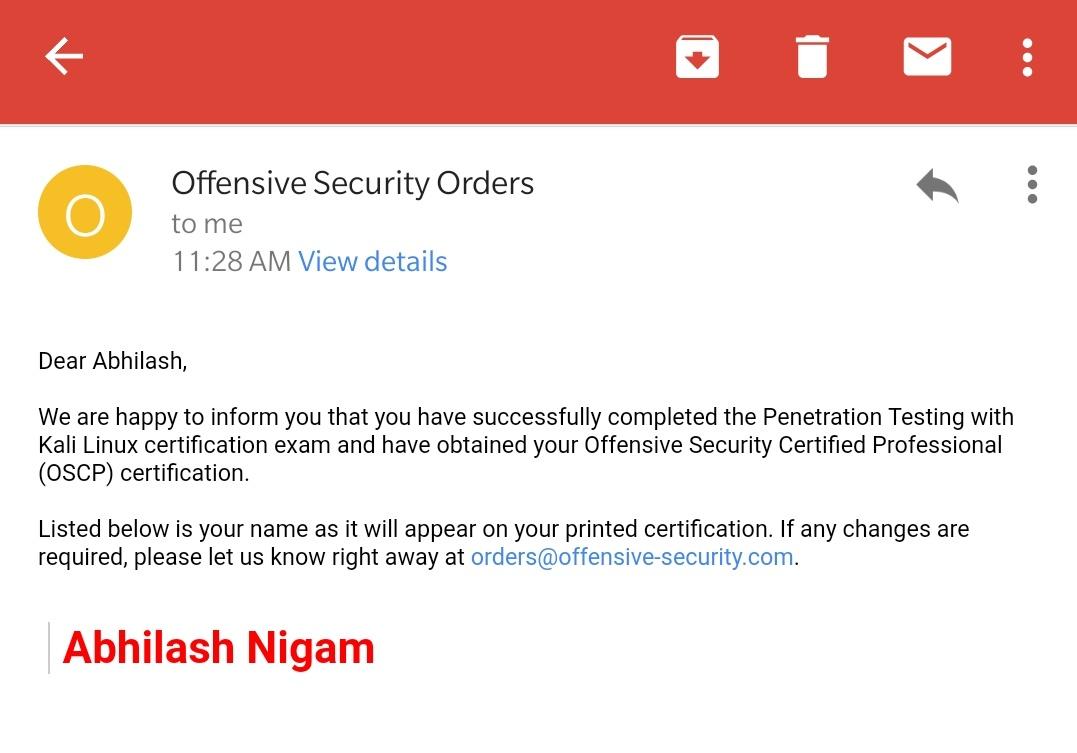
I now hold the OSCP certification and I hold it above all other certs. I put in close to 400 hours of my time into this course, destroyed my social life. It is not that this cert means more than the others, it is because this cert was truly earned. I worked hard for this one and in the process learnt a lot about pen testing, exploitation, and myself. It is an experience that I will never forget.
What Students Should Know
From my entire experience here is what I wish I found on the net before I started.
- When in the labs use metasploit, but every time you do make sure you can exploit the machine by hand as well.
- Do every extra mile exercise, they really do help you learn the material.
- Reach out to other students. Peer support is worth so much. To the guys that supported me thank you! I couldn’t have done it without you.
- When working through the lab keep all exploits you have used on your local machine, neatly organized, and leave yourself readme files of where you found the exploit and which systems it will work on.
- Even though enumeration isn’t as fun and exciting as exploitation PRACTICE it and have good notes. The challenge is pretty much built to fail you if you don’t have good enumeration techniques.
- Make lists and notes to keep yourself on track in the challenge.
- If you are working from a virtual machine, take snapshots of it … you never know when it will break... Mine did, and I wasted a week taking screenshots again.
- Don’t update metasploit when connected to the labs … for some reason it seems to really break it. This happened to myself and one other student that I talked with.
- If you are married or are in a relationship you better hope they are understanding or you will be single by the end.
A big thanks to my partner, family, and friends who helped me through this!